Cancel
Start searching
This search is based on elasticsearch and can look through several thousand pages in miliseconds.
Learn more
TYPO3 is a powerful and highly configurable CMS. The possibilities that you have as a backend administrator are almost endless. However, not every BE user should be an administrator. Too many options bring too many dangers, such as deleting pages that should not actually be edited or when sensitive data in the backend is accessible to every editor. These are reasons for limiting authorizations. But of course a limitation can also be useful to simplify the daily use of TYPO3. The fewer modules, settings and functionalities you see, the clearer the backend will be. In this article, I want to give you a brief overview of the backend authorizations and show you a way to keep track of even complex authorization structures. I will use TYPO3 version 6.2 as a guide, as a list of all TYPO3 versions with all their differences would go beyond the scope of this article.
As already mentioned, there are a huge number of authorization options for BE users. Due to the large number of different functionalities, the following is only a rough list of the possible settings for TYPO3 BE authorizations:
Available modules (page, list, preview, file list, etc.)
Access to tables (view/edit data records)
Available page types (pages, links, folders, etc)
Visible fields from page content (tt_content, tables from extensions, etc.)
Restriction of available plugins (TYPO3, extensions, etc.)
Restriction to the available language
Workspaces
Database shares (page tree)
Directory shares (Fileadmin)
Rights for file operations (read, write, move, delete, etc.)
available categories
Restriction to domain
TSConfig (e.g. hide tabs, set default values, etc.)
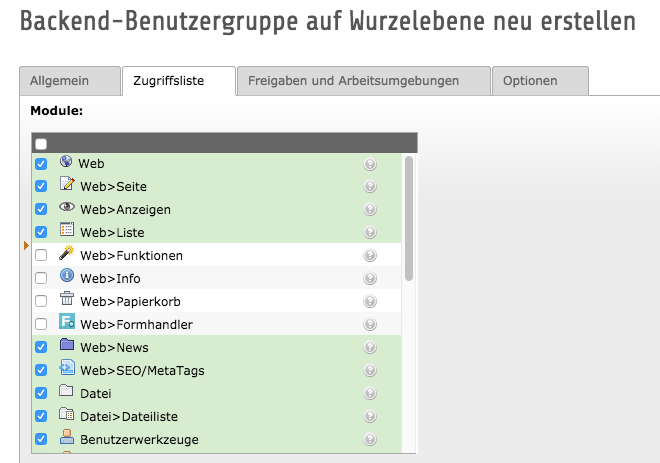
And because the visibility of the page tree can of course also be restricted, there is also the access module with which you can set the following authorizations:
Show page
Edit content
Edit page
Delete page
Create new pages
(+ everything on all subpages)
These authorizations are set to BE groups. More on this later.
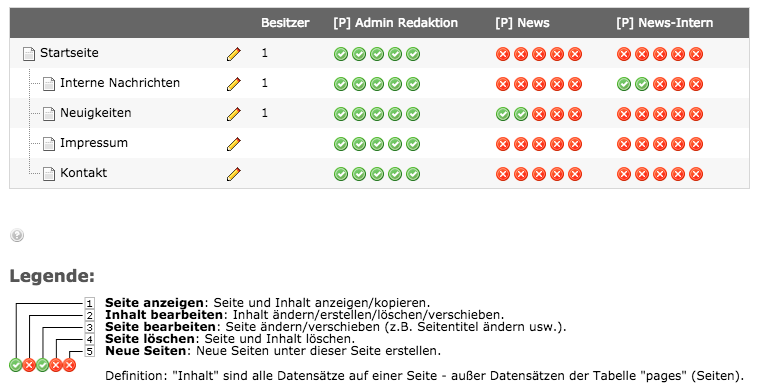
With many different BE user profiles, that's a lot of setting options. To avoid losing the overview here or having to create a separate group for each user, it is advisable to separate the groups logically and group them again . We differentiate between the following types:
Name- Configuration used Purpose
Scheme
| [ACL] Editor | Access Control List | The ACL settings are made in these groups. In other words, which modules, tables, fields and plugins are permitted. |
| [ACL][DISALLOW] Editor | Access Control List DisallowedPlugins | As there are not only authorizations that allow access, but also authorizations that prohibit access, it makes sense to create an extra ACL group for the prohibited plugins. As soon as the BE user has set a plugin as prohibited in his authorizations, this setting cannot be overwritten by another group. |
| [TS] Editor | TSConfig | This group contains all TSConfig configurations. |
| [DBM] Editor | DataBaseMount | This group defines the database mounts and thus the visibility of e.g. sysfolders with data records. |
| [FM] Editor | FileMount | The filemount group is used to release fileadmin folders that the group is to receive. |
| [L] Editor | Language | A limitation to language can be found under ACL but is better placed in a separate group for the sake of clarity. This means that you can see directly in a META group which language authorization is assigned to the group and do not have to search for it in the ACL group first. |
| [EXT] tt_news | Extension | The use of such groups serves to release extension-specific settings. An example of this would be the "tt_news" extension. In this group, it can make sense to set all settings such as ACL, TS etc., as the authorization for an extension is explicitly assigned here. |
| [P] Editor | None(Pagesin the Access module) | This group does not contain any authorizations within the BE group. It is used for the access module to control the page tree permissions in the backend for users with this group. |
| [META] Editor | None | The meta group is the group that combines all the previously mentioned groups in one and has not set any authorizations itself, i.e. it only consists of subgroups (ACL, TS, DBM, P, L, etc.). The advantage here is that, for example, a "[META] Editor" group can be given to the respective editors in the backend and not all required groups have to be assigned to each BE user (ACL, TS, DBM, FM, etc.). |
The naming scheme is always "[KURZEL_DER_BERECHTIGUNGSART] speaking group name".
The respective groups only contain the corresponding authorizations
The groups are named "speaking"
Filtering by authorizations is easy based on the name (e.g. via the database or the TYPO3 backend search for all language groups → "[L]")
A user only ever receives one META group
Assigning a group to a user in the backend is clear, as the list of available groups is alphabetical (and therefore categorized)
This can result in a large number of groups for complex projects
Let's assume we have a new TYPO3 site and the customer has made the following request with regard to BE users:
We need an authorization concept for the new TYPO3 system:
Editorial administrators who can create pages and content
Editors who can only create content
News administrators who can create pages and news items
News editors who can only create news
A user who is responsible for creating and sending the newsletter
Based on this requirement, I would define the groups as follows:
[META] Editorial admin
[ACL] Editor-Admin
[DBM] Editorial office
[FM] Editorial department
[P] Editor-Admin
[TS] Admin
[META] Editorial department
[ACL] Editorial department
[DBM] Editorial office
[FM] Editorial office
[P] Editorial office
[META] News-Admin
[ACL] News-Admin
[DBM] News
[FM] News
[P] News-Admin
[TS] Admin
[META] News editorial office
[ACL] News editorial office
[DBM] News
[FM] News
[P] News editorial office
[META] Newsletter-Admin
[ACL] Newsletter-Admin
[DBM] Newsletter-Admin
[FM] Newsletter-Admin
[P] Newsletter-Admin
[TS] Admin
[EXT] DirectMail
Basically, three main groups are required: one group for page design ("Editorial"), one for news design ("News") and one for the newsletter ("Newsletter"). The page and news design is divided into admins and editors. As the admins have slightly more authorizations than the editors, we need several different groups. If we now compare the editorial groups "[META] Editorial admin" and "[META] Editorial", we notice that the admin group has the same DBM and FM group as the editorial group. As both need to access the same data records (DBM) and files (FM), it does not make sense to create different DBM/FM groups here. The ACL and P groups are different because we do not grant the normal editorial group authorization to create pages (P group) and plugins (ACL group). This is reserved for the "Editorial admin" group. The same applies when comparing the news groups "News Admin" and "News Editorial". The "[TS] Admin" group is a generic group that allows the recursive deletion of pages via TSConfig. A useful setting that is only allowed for the admin groups in this example.
The "[META] Newsletter-Admin" group could of course receive the "[DBM] News" and "[FM] News" group. However, in this example I have decided to explicitly use new groups, as this is a different type of user. In the event that further editorial groups are added, this could lead to further adjustments to the newsletter admin. In my opinion, a clear separation according to functionality makes sense here. In addition, an EXT group for DirectMail is used to release the backend modules of the extension. As limited access to DirectMail modules makes less sense, different access authorizations for the extension are probably not necessary. In addition, the EXT group offers the advantage that the authorizations for DirectMail are more likely to be searched for in this group than under the ACL group, which may have far more different configurations activated/deactivated. It is therefore clearer and easier to handle.
If we now want to know which authorizations user XYZ has, we can roughly find this out via the assigned META group. The more descriptive the group names are, the more practical they are. On the other hand, a name that is too precise, such as "[ACL] News categories (PHP, JS, HTML, CSS)", can provide incorrect information immediately after a change, e.g. if a new news category has been added but the name of the group has not been adjusted.
Let's assume that a few months have now passed and the first adjustments to the BE authorizations have been made:
To ensure that the newsletter admin does not delete any news unintentionally, he must only have the authorization to create a newsletter from the existing news and to be able to send it.
As we have given the newsletter admin its own groups for news access authorization, all other groups remain unaffected by these adjustments. The groups "[P] Newsletter-Admin" and "[ACL] Newsletter-Admin" will be adjusted to grant read-only access to the news.
An area for internal news is required (hidden behind FE Login) and a group that has access to manage this news. Due to the company structure, the normal news authors are not allowed to access this news - neither reading nor editing. In addition, this group should also be able to maintain the regular news.
We therefore need a new group for managing the internal news with access to the existing regular news. The group could be structured as follows:
[META] News-Intern-Admin
[ACL] News-Admin
[DBM] News-Intern
[DBM] News
[FM] News
[P] News-Admin
[P] News-Intern-Admin
[TS] Admin
We use the same groups as the "News-Admin" group and extend these with our own DBM and P groups, as access to the file mount and page tree is required for the internal news. Of course, you could also define the "[META] News-Admin" group as a subgroup. But this has the disadvantage that you have to check the subgroup of a subgroup when making adjustments. Furthermore, the "[META] News-Admin" group could receive changed rights due to another request, which would then also affect this group. You should be able to assume that changes to a META group have no effect on other META groups. This could be seen as a kind of convention.
We need a restriction for editorial users. They may only use the content elements "Text", "Text and image" and "Images". Admins should still have access to all content elements.
The previous permissions only had "allow" settings. For this reason, an additional "ACL-DISALLOW" group is now used, which prohibits permissions on content elements: the "[ACL][DISALLOW] All plugins and special page content" group. This group is now given to the META groups "[META] Editorial" and "[META] News Editorial". This means that the corresponding users only have access to the content elements/plugins that are not prohibited.
The separation of "allowed" and "forbidden" in separate groups is highly recommended. For example, once a certain plugin has been set as "forbidden" within an ACL group, it cannot be enabled again via any other group. The "once forbidden always forbidden" principle then forces us to create a new group for the user, which contains a new - almost identical - ACL group in which the plugin is not set as "forbidden". This would mean double maintenance of the ACL groups and is more error-prone, time-consuming and confusing.
The editorial group needs access to the ExtList plugin.
If we now release this plugin in the ACL-DISALLOW group, the "News editors" group would also have access. As this is not desired, we now need more "ACL-DISALLOW" groups:
[META] Editorial
[ACL][DISALLOW] Everything except text, images and ExtList plugin
...
[META] News editorial office
[ACL][DISALLOW] Everything except text and images
...
Of course, the groups only differ by a tick in the ExtList plugin, but as the "once forbidden always forbidden" principle applies here, I would go down the aforementioned route. Especially when it comes to blocks such as content elements or plugins, it can make sense to outsource them to different groups in order to be able to name the group appropriately and to get an overview of what is prohibited by the group without having to edit the group directly. Depending on the size of the project and the extensions installed, the list of content elements and plugins can quickly become very confusing.
Due to the new branch in England, we need a multilingual website. The authorization must be changed so that users from Germany only have access to German pages and content. Users from England must be able to translate German pages and create their own content in English. The newsletter is only available in Germany.
The requirement has a major impact on our BE authorization. And there are several ways to implement this requirement:
1. Option:
We create the language groups "[L] German" and "[L] English". We then rename the META groups and add a "(DE)" to the name, e.g. "[META] News-Admin (DE)". We then copy the META groups and change the DE to EN. Now the respective META groups must be extended by the respective L group, depending on whether DE or EN.
2. Option:
The META groups remain unchanged and the respective BE users receive the L group for their language.
The second option has the advantage that the number of groups does not increase too much and remains manageable. However, this contradicts the readability of the META groups. The information about which language the BE user is allowed to edit is therefore contained in the user himself and not in the group. My decision here would very much depend on whether there are plans to offer even more languages. There will never be a perfect solution, as it always depends on the ACTUAL and TARGET status of the project.
A good and sensible structuring of the BE authorizations in TYPO3 makes it easy to keep track of and expand them. The administration of BE authorizations is not an easy task for larger projects, but with the necessary discipline and structure it does not have to become an unruly juggernaut.
Anyone who operates a CI/CD infrastructure and repeatedly makes adjustments to BE authorizations will quickly become annoyed. Different database inventories prevent the groups from being exported to the target system and so the changes have to be documented and manually transferred to the respective target system. Even developers and integrators are only human and can make mistakes. Especially when you have to trawl through hundreds of checkbox lists to tick the one box that meets the customer's requirements. This will soon be a thing of the past! The TYPO3 developers are working on making it possible to outsource user authorizations to files. The advantage of this is obvious: versionable BE authorizations. This is perfect for a CI/CD infrastructure and if the configuration files for the user authorizations are also easy to read (perhaps a clear YAML file?), the documentation for the authorizations (which is outdated again at the latest after writing) is also no longer necessary.
P.S.: And thanks to Daniela Grammlich for sketching the cover picture. If you want to see more sketchnotes, go here: https://grammheimlich.de/
It's quite likely that one or two questions remain unanswered, as the theme is quite complex. Please do not hesitate to ask in a comment or contact us directly by phone: 0721 - 91090.
We are happy to help.