Cancel
Start searching
This search is based on elasticsearch and can look through several thousand pages in miliseconds.
Learn moreKeycloak is a real all-rounder, combining single sign-on (SSO), identity brokering/social login and user federation under one roof - and all in open source!
We have been using Keycloak for identity and access management in our customer projects for many years.
Keycloak is license-free and offers many organizational and functional advantages for your company.
Our specialists will be happy to support you both conceptually and practically in the implementation of your new Keycloak infrastructure.

Our specialists will support you from the beginning to the end of your Keycloak project and will assist you with their many years of experience and expertise. Even after successful implementation, our specialists are at your disposal for ongoing operation, adjustments, further developments and training.
Our specialists offer you
As open source software, Keycloak is license-free, even with thousands of accounts and parallel users. This results in a considerable cost advantage over commercial solutions.
Keycloak allows users to successfully log in once and then automatically grants them access to all applications integrated with Keycloak without having to log in again. This also applies to user logouts. This improves the user experience and reduces the complexity of passwords and login processes.
As Keycloak is an open source solution, companies are not tied to a specific provider. They have the freedom to adapt and expand the platform according to their needs.
Keycloak offers various security features such as multi-factor authentication (MFA) to provide additional layers of user identity. With WebAuthn support, users can verify their identity with FIDO2-compatible security keys or biometric features.
Keycloak is supported by a large and active community and is widely used in many organizations. This broad acceptance results in a stable and well-supported platform that is continuously being developed.
Keycloak supports common authentication and authorization protocols such as OpenID Connect, OAuth 2.0 and SAML 2.0 and can be easily integrated with many applications and services that use these protocols.
Keycloak offers extensive customization options so that you can adapt the system to your specific requirements and business processes. We can make technical adjustments to your needs by using APIs and extension points. The appearance can also be designed according to your specifications.
Keycloak offers a central administration console that allows you as an administrator to manage users, groups, roles and access policies. The console also provides detailed insights into the activities and security events in the system.
With Keycloak it is possible to integrate various identity providers and directory services such as LDAP, Active Directory and other IAM systems. In addition, it offers social login options where users can use their social media accounts to log in.
Keycloak was developed to deliver high performance and meet the requirements of companies with large numbers of users. The system is not only very scalable, but also has robust caching mechanisms. As a result, it remains very performant even under high load. We will be happy to support you with the right architecture for your company.
Keycloak supports operation in a cluster to ensure high availability and load balancing. This allows companies to ensure that their IAM infrastructure is always available, even if individual nodes fail.
Keycloak can be easily deployed in container orchestration platforms such as Docker and Kubernetes. This facilitates the scaling, operation and management of Keycloak instances (e.g. also for a cloud infrastructure)
Keycloak offers developers a wide range of extension points and APIs to customize and extend the platform according to their needs. This allows you to seamlessly implement additional functions and integrations.
With Keycloak as part of your infrastructure, you have the option of managing individual applications (e.g. websites, CMS, stores, portals, etc.) in a user-friendly way with one login. Users identify themselves once via Keycloak and are no longer forced to enter their username and password for each application individually (SSO). The same also applies to logging out. A single logout is sufficient to log out of all applications connected to Keycloak.
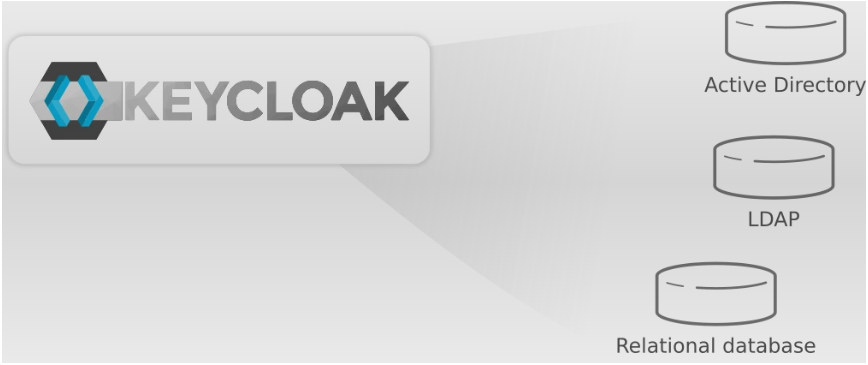
Keycloak is able to connect to your company's existing LDAP or Active Directory (AD) servers. Other providers or relational databases can also be integrated into Keycloak. The system is therefore extremely flexible and in many cases no major adjustments to the existing user administration or infrastructure are necessary.
Simple login with a social media account is also no problem with Keycloak. If you have OpenID Connect, SAML 2.0 or Kerberos as an identity provider, these can also be integrated.
